If you need to know when a server’s public certificate will expire, use this:
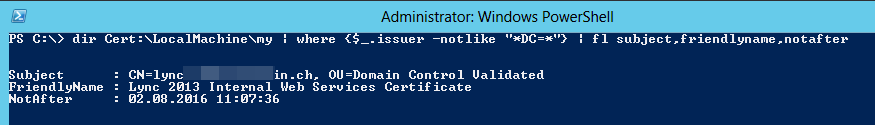
dir Cert:\LocalMachine\my | where {$_.issuer -notlike "*DC=*"} | fl subject,friendlyname,notafter
This assumes that your internal Certification Authority has an LDAP name (Windows based CAs usually do), so we’re looking for certificates NOT issued by such a CA. The next step would then of course be to automate this, for example have this script run on a daily basis, read what’s in the “NotAfter” property and alert an administrator 30 days in advance to make sure transitioning to a new certificate will not cause the service to be interrupted.
